The oldest email I had on my Mac was dated January 1st, 2006. That was in an archive folder for my iCloud email. ((What’s great is that the email was to a buddy talking about using group iDisk and iCal for a project we were working on. Man, did Dropbox simplify things.)) Now, what’s the point of mentioning that? Well if you got a hold of my iPhone, and guessed the four-digit passcode, you essentially would have access to every email I have received since that date. All neatly stored in my archive folders, totaling well over 50,000 messages — attachments included. A good chunk of my digital life.
You don’t need NSA computing power to read all my emails. You could get a full archive by getting into any of my iOS devices, getting into my email server, or getting into my Mac. Some of those things I can properly secure. Some (most?) are almost impossible to secure completely. I’m guessing my passcode wouldn’t be too hard to guess if you just recorded me for a few hours — you’d probably get it in fifteen minutes and I wouldn’t notice.
That bothered me from the geeky “I wonder if I can secure that” perspective. So that’s what I set out to change.
I searched around to see if there was a way to encrypt the mail database stored on my OS X Server providing email services — there are, but none that I understood. Even still, those methods wouldn’t secure my iOS devices, or my iCloud archive. *Damn*.
It’s also been making me uneasy that my Mac mini is sitting there with no encryption — as encryption would make it very difficult to remotely administer a Mac, given that I have no way of physically getting to that Mac.
The solution then seemed to present itself: get the data off of the Macs, iOS devices, and Servers. Take my email archive out of IMAP and into something that is encrypted. I then thought about how I use that archive right now: reference. Even just for reference Mail.app does a piss poor job of searching, finding, and displaying old email messages. So Mail.app actually is a pain in the ass for managing my email archive.
I began searching for email archiving applications that I could use to achieve my goal. None of them offered encryption, more on that later, but I found three applications to try: [MailSteward](http://www.mailsteward.com), [Mail Archiver X](http://www.mothsoftware.com), and [Email Archiver](http://emailarchiverpdf.com) (which is least like the others).
## Email Archiver
You can find this on the Mac App Store for $24.99. It takes a range of emails and converts them to searchable PDFs. This sounds appealing for future safety, but in practice this is very slow, and very useless for referencing archived files. I quickly gave up on this app.
This app is better suited for archiving things project by project — if you are wont to do that.
## Mail Archiver X
Strike one was the lack of retina capability, but Retinizer quickly solved that. In fact the biggest issue I have with Mail Archiver X is that the search capabilities are lacking. In Mail Archiver X you get just one search box, much like Mail.app which I have already mentioned sucks at search.
This was ultimately the reason I steered clear of Mail Archiver X.
## MailSteward
Obviously, with the other two out, I chose MailSteward. I chose it because of it’s search power, which looks like this:
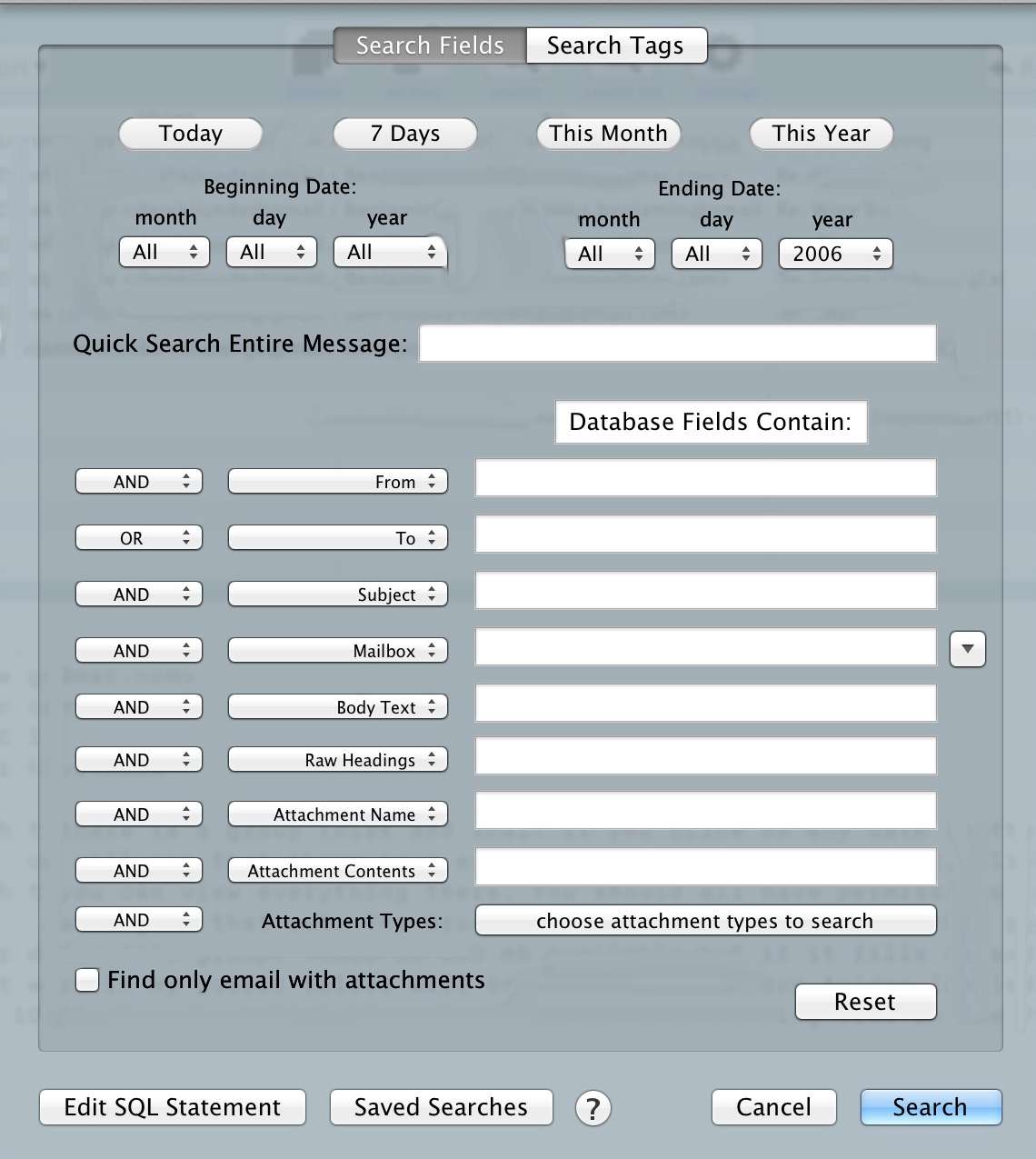
That’s a powerful tool, especially given that my dataset is 50,000 emails — some with attachments. There’s a ton of great options in the app, including scheduled archiving and auto-tagging (which I have yet to implement). Overall I ended up with a database well over 15GBs, but a program that can search it faster and better than Mail.app could.
So now I have a better search method stored locally on my Mac.
## The Result
This solution does not solve every problem. While it offers better search of my email archive, there are still a bunch of new issues that popped up. Here’s the system I currently have in place:
– My MacBook Pro archives email in everything except my inbox daily at 10:21pm.
– My Mac mini also has a copy of MailSteward installed and it archives everything once a month from all inboxes to a local database.
– I have mail rules set to delete any email over six months of age. ((These rules are pretty hit and miss. So far I had to do the initial delete manually.))
Therefore, at most, someone could grab the last six months of my email. As I get more comfortable with this system I plan on shortening that time period to one month for personal stuff, one week for this blog, and two months for work.
Now, you may ask, what about the database for MailSteward sitting on your Mac mini? Well, that database sits *inside* a Truecrypt volume. ((My MacBook Pro is encrypted by FileVault 2, which is good enough for that database.)) I just have to remember to mount that volume before MailSteward wants to run each month, or after restarting the machine (which I typically only do for software updates).
All of this means I get no access to old emails from iOS, ((I *could* VNC into my Mac mini and search that way if I want.)) but it also means that I have secured my old email from people who gain physical access to my devices.
Yes, the NSA *might* already have copies of my stuff, but that’s no reason to make it easy for someone who gets access to my devices to have a robust database on me.
Overall, this is a far better solution for people that like to search their email archive, and it *can* be more secure if you set it up correctly. I was, however, a bit uneasy deleting all those emails and relying only on MailSteward.
