Year: 2013
-
Quote of the Day: Brent Simmons
“One way of looking at Google Glass: now the surveillance state can see through your eyes. Even when you blink.” -
‘Three things I learned from the Snowden files’
Jay Rosen:
> The point holds for collecting phone records. Even if no one in the government reviews whom I’ve called or texted, my liberty is violated because “someone has the power to do so should they choose.” Thus: It’s not privacy; it’s freedom. But “freedom advocates” would be an awkward construction in a news story.
-
‘Apple Says It Has Never Worked With NSA To Create iPhone Backdoors’
Matthew Panzarino:
> Apple has contacted TechCrunch with a statement about the DROPOUTJEEP NSA program that detailed a system by which the organization claimed it could snoop on iPhone users. Apple says that it has never worked with the NSA to create any ‘backdoors’ that would allow that kind of monitoring, and that it was unaware of any programs to do so.
Click through and read the statement — it’s a pretty definitive statement from Apple (and came quickly, for Apple at least) and encompasses *all* Apple products not just the iPhone.
This doesn’t mean there isn’t a backdoor — as I understand it the NSA attacks BIOS level software. If that is the case perhaps Apple isn’t writing the BIOS’ on iPhone and therefore the NSA has partnered with an Apple vendor? This is pure speculation though.
-
Côte&Ciel Isar Rucksack
Andrew Kim has a review up on Minimally Minimal of the Isar Rucksack. While I don’t think this is a bag I would enjoy, it is certainly very unique (and beautiful, no doubt in part due to Kim’s beautiful photography).
-
So You Thought DigitalOcean Was Great?
I’ve never used DigitalOcean (and I’m glad about that), but I’ve been hearing about many people loving their service. There was an issue [posted on GitHub](https://github.com/fog/fog/issues/2525) detailing a flaw in the way user data was deleted from DigitalOcean servers. This flaw lead to data being “leaked” between user accounts. The discussion was then moved over to DigitalOcean [here](http://digitalocean.uservoice.com/forums/136585-digitalocean/suggestions/5280685-scrub-vms-on-delete-by-default).
Essentially all data could be wiped, but it required the user to check a specific box, or call a poorly documented part of the API — in other words it was a bad design decision from DigitalOcean. This isn’t good at all, as Apache logs were being pulled from other user accounts.
However, [DigitalOcean’s response was horrible](https://digitalocean.com/blog_posts/transparency-regarding-data-security). Instead of owning the issue and making a change, they offered a qualified excuse, committed to changing, and then (if the comments are any indication) lied about data being leaked.
Here’s what DigitalOcean said in their post:
> At no time was customer data “leaked” between accounts.
Jeffrey Paul’s comment on that same post:
> For fuck’s sake, now you’re just lying.
> Not scrubbing has been the default – a user doesn’t have to “explicitly not scrub”.
> If no customer data leaked between accounts, how was I able to read someone else’s stack traces[1], web logs[2], and customer tokens[3] on a freshly provisioned VM? (I am the person who got bitten by this dark pattern, investigated further, verified your error, filed the bug in fog, and then spent half my Monday auditing credentials because you LEAK DATA BETWEEN CUSTOMERS.)
> What follows is evidence to directly support the claim that you’re lying through your teeth to save face after having been caught being grossly irresponsible with your customers’ data.
> Please start acting like professionals.
> [1] http://i.imgur.com/TMp2kdf.png
> [2] http://i.imgur.com/WLv2qSE.png
> [3] http://i.imgur.com/fJOxRN9.png
There’s a few other comments supporting his claim too.
I’d run away from DigitalOcean if I was using them.
-
‘The Products Apple Doesn’t Have Time to Improve’
Marco Arment:
> While most of the press demands new hardware categories, I’d be perfectly happy if Apple never made a TV or a watch or a unicorn, and instead devoted the next five years to polishing the software and services for their existing product lines.
On this, I am in complete agreement with Arment. See also [Arment’s follow-up (of sorts) post](http://www.marco.org/2013/12/29/smart-watches-and-face-computers) on smart watches and Google Glass.
-
Reminder: December Yearly Membership Discount
Just a quick reminder that you can save $10 on a yearly subscription to this site through the end of tomorrow. This isn't likely something I will do again so now is your chance (as they say).
Thanks for your support — it is your support that will hopefully pay the bills one day.
-
‘The NSA has nearly complete backdoor access to Apple’s iPhone’ [Updated]
Jay Hathaway:
> According to leaked documents, the NSA claims a 100 percent success rate when it comes to implanting iOS devices with spyware. The documents suggest that the NSA needs physical access to a device to install the spyware—something the agency has achieved by rerouting shipments of devices purchased online—but a remote version of the exploit is also in the works.
UPDATE: [Steve Wildstrom reports](http://techpinions.com/apple-iphone-and-the-nsa-a-tale-of-sorry-journalism/26125):
>If you dig back through the sources here, you find a fascinating dump of documents in Der Spiegel (German original) about the NSA’s Tailored Access Operations including a 50-page catalog of snooping devices worthy of MI-6′s fictional Q. One, called DROPOUTJEEP, claimed the ability to compromise an iPhone by replacing altering its built-in software. “The initial release of DROPOUTJEEP will focus on installing the implant via close access methods,” the 2008 document said. “A remote capability will be pursued in a future release.” In other words, before any snooping took place, the NSA first needed to get its hands on your iPhone and replace its software1 .
-
‘What I Didn’t Say’
Paul Graham following up on a controversial quote that was attributed to him from the $400/year *The Information*:
> “We” doesn’t refer to society; it refers to Y Combinator. And the women I’m talking about are not women in general, but would-be founders who are not hackers.
> I didn’t say women can’t be taught to be hackers. I said YC can’t do it in 3 months.
> I didn’t say women haven’t been programming for 10 years. I said women who aren’t programmers haven’t been programming for 10 years.
> I didn’t say people can’t learn to be hackers later in life. I said people cannot at any age learn to be hackers simultaneously with starting a startup whose thesis derives from insights they have as hackers.
Of all people [Michael Arrington has a good take on the situation](http://uncrunched.com/2013/12/30/the-disinformation/):
> And really, three sins were committed. The first was changing a quote. You just can’t do that, ever. The second was omitting contextual information which would have made the statement intelligible. And the third was taking a background discussion about Paul’s partner Jessica Livingston and turning it into an “interview” in the first place.
UPDATE: [Jessica Lessin has posted about this on her personal site](http://jessicalessin.com/2013/12/31/on-the-information-and-how-we-operate/) (not the site in question). It’s a shit defense, and her reasoning for editing his quote makes zero sense — unless of course sensationalism is what they wanted.
-
‘BlackBerry CEO: Here’s our new strategy’
John Chen CEO of BlackBerry:
> Today, our company is strong financially, technologically savvy and is well-positioned for the future. In less than two months, my team and I have engineered a new strategy to stabilize the company, return to our core strength in enterprise and security, and maximize efficiencies.
That’s all you need to know about the new strategy: it was *engineered*. I think that word alone encompasses why BlackBerry is failing so quickly. They are making data driven decisions, and not decisions that create an emotional connection between the user and the device. In other words: they are trying to accomplish a task, a feature, and not trying to generally make life better for the user.
This is a concept you either get, and therefore accept, or one you don’t get and flat out reject — there’s little middle ground that I can see in the “make life better” business mindset that Apple is preaching.
But, since we have extra words in Chen’s post, allow me to point out two more things:
> When it comes to enterprise, we’re still the leader. Don’t be fooled by the competition’s rhetoric claiming to be more secure or having more experience than BlackBerry. With a global enterprise customer base exceeding 80,000, we have three times the number of customers compared to Good, AirWatch and MobileIron combined. This makes BlackBerry the leader in mobile-device management.
He plays up security the most, but let’s remember that reports are the NSA has a backdoor into BlackBerry servers (likely all devices). At this juncture in time I think it is highly irresponsible to tout digital security.
Lastly:
> In the last 60 days, more than 40 million new iOS and Android users have registered to use BBM. We will continue to invest in this popular service and build out its features and channels, with plans to turn it into a revenue stream in the coming years.
All 40 million of which *used* to be using BlackBerry devices — not sure that is a “win” there Mr. Chen.
-
‘US Struggling to Keep Pace in Broadband Service’
Edward Wyatt:
> In Riga, speeds average 42 megabits a second, but many users had service of 100 to 500 megabits as of mid-December, according to Ookla. In San Antonio, broadband speeds average 16 megabits a second. Higher speeds are available through cable TV and phone companies, but the expense is such that many households cannot afford a connection.
There’s another side that these reports often gloss over: upload speed. When everyone first got on the web download was paramount because the web was mostly consumption. I’d argue that now most people also *add to* the web in the form of photos, videos, etc being uploaded. In the US a standard Comcast internet service account is likely 20mbps guaranteed down, and 5mbps guaranteed upload speeds. That is sad.
Even my upgraded Comcast service nets me just 50mbps down and 20 mbps up — and I pay a price for that which most people would flat out refuse to pay.
Faster internet services are among one of the few reasons left to live in densely populated areas.
-
What is the Future of the Open Web?
Tyler Fisher:
> I don’t pretend to have all the answers, but here is a crucial aspect: web services cannot exploit the general user’s ignorance about the web. Even if users do not care about owning their data or understand what owning their data means, the web service cannot take advantage of that and sell their data. This is where the social web has failed us. The social web has exploited the ignorance of the average user of the web for profit.
-
‘Inside TAO: The NSA’s Shadow Network’
Jacob Appelbaum, Laura Poitras, Marcel Rosenbach, Christian Stöcker, Jörg Schindler And Holger Stark reporting for Spiegel on the NSA TAO operations:
> A comprehensive internal presentation titled “QUANTUM CAPABILITIES,” which SPIEGEL has viewed, lists virtually every popular Internet service provider as a target, including Facebook, Yahoo, Twitter and YouTube. “NSA QUANTUM has the greatest success against Yahoo, Facebook and static IP addresses,” it states. The presentation also notes that the NSA has been unable to employ this method to target users of Google services. Apparently, that can only be done by Britain’s GCHQ intelligence service, which has acquired QUANTUM tools from the NSA.
And:
> Take, for example, when they intercept shipping deliveries. If a target person, agency or company orders a new computer or related accessories, for example, TAO can divert the shipping delivery to its own secret workshops. The NSA calls this method interdiction. At these so-called “load stations,” agents carefully open the package in order to load malware onto the electronics, or even install hardware components that can provide backdoor access for the intelligence agencies. All subsequent steps can then be conducted from the comfort of a remote computer.
The last quote makes a lot of sense, and is likely the reason why people like Schneier went and bought a computer from a store with cash as it’s not likely to have been intercepted. The first quote block though shows the amazing toolset at the TAO’s disposal.
-
ANT Division
Jacob Appelbaum, Judith Horchert and Christian Stöcker:
> These NSA agents, who specialize in secret back doors, are able to keep an eye on all levels of our digital lives — from computing centers to individual computers, from laptops to mobile phones. For nearly every lock, ANT seems to have a key in its toolbox. And no matter what walls companies erect, the NSA’s specialists seem already to have gotten past them.> This, at least, is the impression gained from flipping through the 50-page document. The list reads like a mail-order catalog, one from which other NSA employees can order technologies from the ANT division for tapping their targets’ data. The catalog even lists the prices for these electronic break-in tools, with costs ranging from free to $250,000.
-
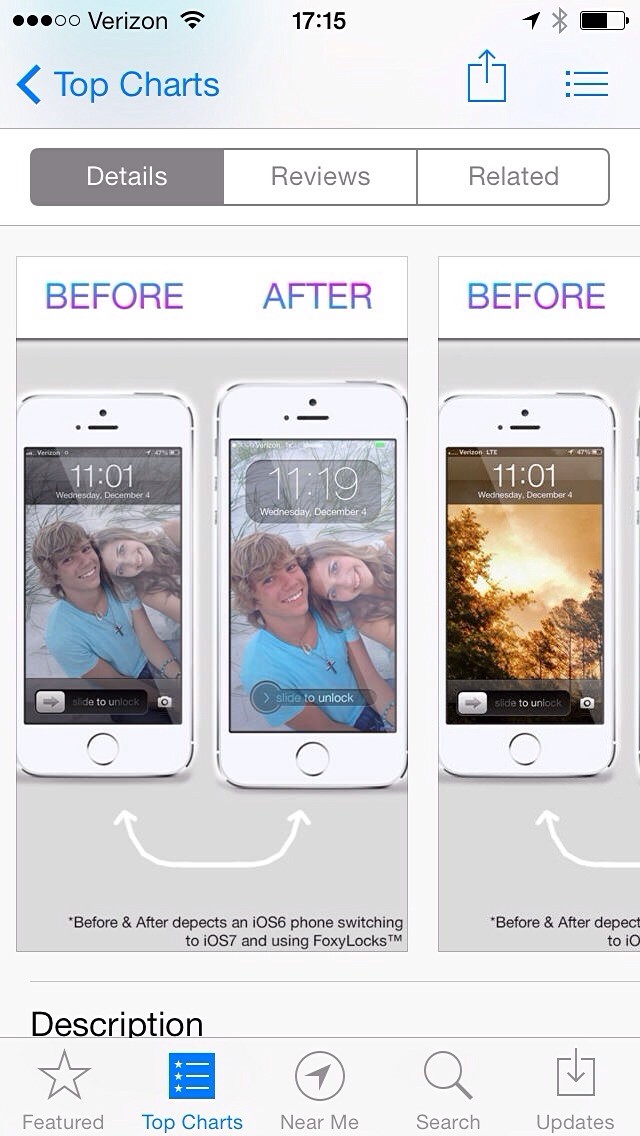
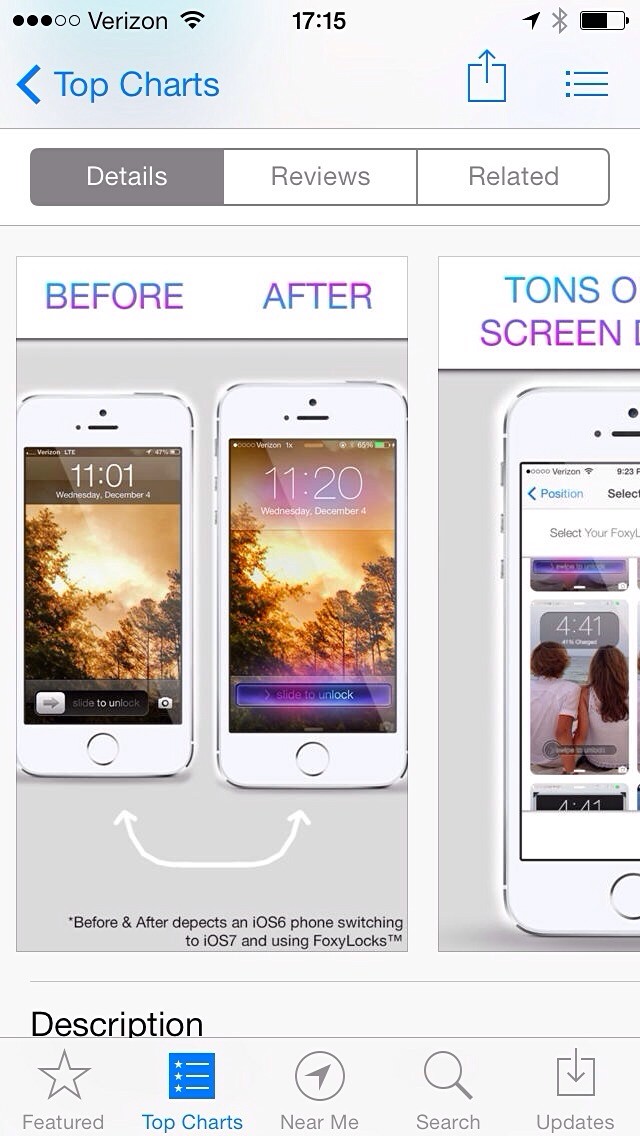
Today in Misleading App Store Screenshots: FoxyLocks
I regularly browse through the top apps just to see what kind of crap people are downloading, but today I came across a real gem in [FoxyLocks](https://itunes.apple.com/us/app/foxylocks/id773956272?mt=8).
Don’t bother clicking that, it’s an app that claims to change the appearance of the iOS lock screen. Now, when you stop chuckling, take a look at the screenshots they provide:
It’s pretty easy to guess what the app is doing: you pick your wallpaper photo and it overlays some crap to make it look like you are framing the content on the lock screen (though I bet this doesn’t work well with parallax, but who cares).
What’s really great is that you will notice the image they want downloaders to assume is the “before” image is, in fact, from iOS 6 and the “after” is iOS 7. They say it right at the bottom in fine print, but no one reads that.
This is the exact kind of bullshit misleading marketing that I would *expect* Apple to be weeding out of the App Store. It’s just trash marketing that should get developers banned.
-
‘Do You Want to Write?’
[Michael Lopp, writing about Writer Pro](http://randsinrepose.com/archives/do-you-want-to-write/):
> Preferences are a sign of design laziness; they are an indication the people responsible for building the application don’t have enough empathy or desire to do the work they intend to be paid for: design the application so I that I can work, not think about how I might work.He listed Word, Excel, and Photoshop as examples of “kitchen sink” apps which are packed full of features. I’d add to that list OmniFocus. I think the above quote encapsulates my issues with a lot of apps these days in general.
I’d recommend ignoring all the ridiculous stuff going around about patents surrounding Writer Pro (they’ve wisely decided to drop the whole thing) and just check out the app, especially if you make software. Writer Pro is an exercise in stripping an app down to what is needed, not what is asked for.
There’s an old adage about how we got cars with tail fins in the mid-1950s. It goes something like this: “instead of asking people what they wanted in a new car, they started asking people what their neighbor would buy.” And then we got cars with fins.
I can’t find a reference for this, but the adage seems to encapsulate the design decisions of a lot of software. Designing what *you* think the user wants instead of pairing things down to only what the user actually *needs*. It feels nearly impossible to do at times, especially if you dislike people emailing you screaming for features. But I think it is the direction that good, nay *great*, software is headed.
-
‘Automatic Document Redaction with PDFpen’
Great tip from Katie Floyd — I had no idea this could be automated.
-
‘NSA mass collection of phone data is legal, federal judge rules’
The Guardian:
> US district judge William Pauley said the dragnet program “represents the government’s counter-punch” to al-Qaida in the wake of the 9/11 terror attacks. The decision conflicts with a ruling in another case, increasing the likelihood that the US supreme court will take up the issue.
I think the best thing that can happen is for the Supreme Court to rule on this — one way or another we need an open court ruling and the Supreme Court is the best court to hand down this ruling.
-
Chill
[Jonathan Poritsky, in his well linked to take on Writer Pro](http://www.candlerblog.com/2013/12/23/no-thanks-ia/):
> When I hand my money over to a developer, I want to at least feel like I’m the reason their product exists, that it otherwise wouldn’t but for my interest, support and cash. Goading other developers into forking over licensing fees undercuts that feeling for me. While the full patent application isn’t available yet, Reichenstein tweeted an image that has “Method of editing text in a text editor” listed as the “Title of Invention.” That sounds precisely like the sort of broad software patent that discourages innovation.
I think the tactics iA is allegedly going to take is lame. But there’s a few small thoughts that I want to point out because I think we may be a bit premature here:
1. Getting a patent isn’t bad. It’s likely the smartest move to protect yourself from other patent trolls. You fight nukes with nukes. iA didn’t start it, they likely just want to survive.
2. Upon introducing the iPhone Steve Jobs made a snarky comment about all the patents in it. I don’t remember anyone doing anything but applauding him. Or doing anything but applauding their victory over Samsung. The size of the players shouldn’t change your “moral” stance.
3. I don’t believe anyone has been sued over this yet.
4. What if the licensing fee is *actually* reasonable and the US affirms the patent? Nothing much to complain about.As far as I can see, the worst iA has done is a shitty PR campaign. Maybe they can add PR tools into the next Writer update.
We aren’t patent experts, we are bloggers. ((I’ll amend this to say some bloggers are patent experts. But I haven’t seen them chime in on this.)) Until something actually happens I say we simmer down a bit.
-
‘A free distraction’
Dr. Drang:
>Many of us aren’t writers, per se, but we end up doing a lot of writing to communicate what our real jobs are. This utilitarian writing often consists of taking a mound of disparate facts and explaining them through organization. This is a complex process that’s hard to do in an information-free writing environment.He’s got good thoughts on distraction free writing tools. I try not to get caught up in the ideology behind these apps, and instead focus on whether or not they meet my needs better than other tools. So far, writing in an app like Pages or TextMate is more annoying to me than Ulysses or Writer (Pro). The good doctor is right, as it does come down to how you write.